Encrypted container setup
Next choose volume option in menu, and create a encrypted file container.

We will choose to create a standard volume here, since this is only for inheritance nor for fighting CIA.

Choose a location to save your container and then continue
For the encryption algorithm I strongly recommend to choose multiple encryption layers, since this prevents an algorithm is backdoored or broken in the future.

For the volume size just choose 10MB since this is only for saving a piece of text

Then create a strong and easy to remember password at this step

Next choose the key file option

We will try to generate 3 random keyfiles
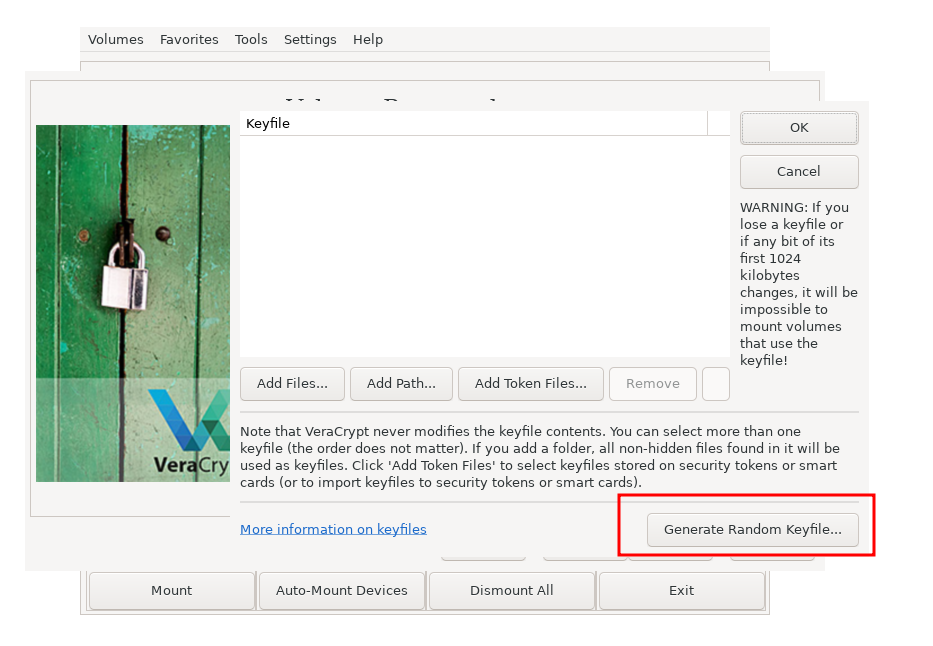
Move your mouse to collect enough entropy, this is very important! The protection from cryptography will be significantly weakened if there is not enough randomness. Then set the key file size to maximum which is 1048576. This is the maximum size utilized by veracrypt and we should use that.

Name your keyfile as key 1 and save it. And repeat this step to produce key 2 and key 3, we will use them later
If you have done this correctly, you should have 3 key files like this

Then come back to the creation of container 1, choose the use keyfiles option

Select keyfile 1 and keyfile 2 as planned in the theory part


At the format stage move your mouse like what you have done for keyfile, and then format the volume.

Now you have completed the setup of container 1, just repeat the above steps, using the same password but with different combination of keyfiles as stated in the theory part. You should get container 2 and container 3 after this.
Inheritance
After all the hard work, now we will store the seed.
You should try to decrypt your containers to make sure they really work!

Select container 1 in the menu, select a slot and click mount

Then enter the password, and insert the keyfiles


Click ok and if nothing goes wrong your container should be decrypted and visible in the file explorer.
Now copy your seed into the container and unmount it. You should repeat those above steps, test container 2 and container 3, and copy the seed into them.
All the work is done now, you should pack up all the containers, put them in a hdd or burn them on a cd, and do a cloud backup of containers(do not upload your keyfile!). Store the keyfile 1 with your local copy of containers, and write done the password and notify your family members. If your family members are not familiar with crypto or programming, you should also write down a detailed note how to decrypt the container plus how to restore monero with seeds, and possibly how to dump them on kraken to convert back to fiat :-(
Final step is to contact two independent lawyers in different countries, and send them a physical copy of your keyfile. Now you can comfortably sleep, because you know your crypto will still be used by someone when God judges your life in heaven.























