mirror of
http://git.nowherejezfoltodf4jiyl6r56jnzintap5vyjlia7fkirfsnfizflqd.onion/nihilist/hacking-blogposts.git
synced 2025-05-16 04:16:59 +00:00
13 KiB
13 KiB
Offensive Security Writeups (NO LONGER MAINTAINED)
Hack The Box is an online platform allowing you to test your penetration testing skills and exchange ideas and methodologies with thousands of people in the security field.
Below you will find my personal writeups of the various boxes that can be found on hackthebox.eu, ranked by difficulty.
Hack The Box - Easy Boxes
- ✅ - Lame
- ✅ - Legacy
- ✅ - Devel
- ✅ - Beep
- ✅ - Optimum
- ✅ - Arctic
- ✅ - Grandpa
- ✅ - Granny
- ✅ - Bank
- ✅ - Blocky
- ✅ - Blue
- ✅ - Mirai
- ✅ - Shocker
- ✅ - Sense
- ✅ - Bashed
- ✅ - Nibbles
- ✅ - Valentine
- ✅ - Sunday
- ✅ - Bounty
- ✅ - Jerry
- ✅ - Active
- ✅ - Access
- ✅ - Frolic
- ✅ - Curling
- ✅ - Irked
- ✅ - Teacher
- ✅ - Help
- ✅ - FriendZone
- ✅ - Netmon
- ✅ - CasaDePapel
- ✅ - Bastion
- ✅ - SwagShop
- ✅ - Writeup
- ✅ - Haystack
- ✅ - Safe
- ✅ - Heist
- ✅ - Networked
- ✅ - Forest
- ✅ - Postman
- ✅ - Traverxec
- ✅ - OpenAdmin
- ✅ - Nest
- ✅ - Traceback
- ✅ - Remote
- ✅ - Servmon
- ✅ - Admirer
- ✅ - Blunder
- ✅ - Tabby
- ✅ - Buff
- ✅ - Omni
- ✅ - Doctor
- ✅ - Academy
- ✅ - Laboratory
- ✅ - Luanne
- ✅ - Delivery
- ✅ - Toolbox
- ✅ - Sauna
- ✅ - ScriptKiddie
- ✅ - Armageddon
- ✅ - Spectra
- ✅ - Love
- ✅ - Cap
- ✅ - Knife
- ✅ - Previse
- ✅ - Paper
- ✅ - BountyHunter
- ✅ - Explore
- ✅ - Horizontall
- ✅ - Backdoor
- ✅ - Driver
- | CVE-2007-2447, vsftpd 2.3.4
- | ms08_067_netapi RCE
- | Anonymous FTP, ms10_015_kitrap0d
- | Elastix, Webmin, vtiger
- | HttpFileServer 2.3, rejetto, 41020
- | ColdFusion 8, JRun Web Server
- | IIS 6.0, webdav
- | IIS 6.0, webdav
- | DNS, reverse php shell, root binary
- | Wordpress, jar
- | MS17-010, EternalBlue, Win7 SP1
- | PiHole
- | ShellShock, 34900
- | FreeBSD, pfSense
- | PHPBash, kernel 4.4, 44298
- | NibbleBlog 4.0.3
- | HeartBleed
- | Solaris, SunOS, fingerd, unshadow, john
- | IIS 7.5, transfer.aspx
- | Tomcat, tomcat_mgr_login, mgr_upload
- | SMB, Kerberoast, gpp encrypt
- | ftp, telnet, pst, mbox, readpst, runas
- | Brainfuck, nginx, ROP exploit
- | Joomla , reverse php
- | UnrealIRCd
- | Moodle, MariaDB, hashes
- | HelpdeskZ, reverse php, 44298
- | smb, ssl certs, dns
- | ftp, prtg network monitor
- | ssl certs, cron
- | smb, share mounting, vhd, mRemoteNG
- | Magento, lfi, reverse php
- | CMS made Simple, 46635 , reverse py
- | Elasticsearch, json, kibana
- | ROP, ghidra, gef, keepass hashes
- | Cisco pass, smb, sysinternals
- | Reverse php gif, cmd execution
- | BloodHound AD Navigation, Exchange Windows
- | Redis 4.0.x, Webmin 1.910, RCE
- | nostromo 1.9.6, journalctl
- | OpenNetAdmin, nano shell
- | Visual Basic, SMB, telnet
- | Web-Shells, SSH Motd script
- | Umbraco v7.12 ,TeamViewer v7
- | xc.exe, nsclient++, ftp, winpeas
- | Adminer, MySQL, Python library Hijacking
- | Bludit 3.9.2, SHA1, sudo 1.8.25p1
- | Tomcat, LFI, lxc container
- | Gym Management RCE, Buffer Overflow
- | Windows IOT, SirepRAT.py, Import-CliXml
- | XML SSTI splunkd RCE
- | PHP Laravel token deserialization, composer
- | Gitlab CE 12.8.1 gitlab-rails, SUID bit
- | NetBSD lua code injection, doas, netpgp
- | OSTicket, Mattermost, hashcat custom list
- | SQL Injection reverse shell, boot2docker
- | LDAP, kerberos, mimikatz, NTLM hash
- | Msfvenom apk exploit, command injection
- | Drupal7, MySQL password hash, Snap GTFOBin
- | .save extension, Wordpress, initctl privesc
- | nishang ps1, AlwaysInstallElevated msi msfvenom
- | pcap, python3.8 cap setuid capabilities
- | php 8.1.0, 49933.py, knife binary
- | auth bypass, code injection
- | Wordpress 5.2.3, CVE-2021-3560
- | xml poisoning, python poisoning
- | ES File Explorer, adb shell
- | strapi, laravel 8
- | ebook-download, gdbserver, screen
- | MFP firmware, RICOH_PCL6
Hack The Box - Medium Boxes
- ✅ - Popcorn
- ✅ - Bastard
- ✅ - Tenten
- ✅ - Cronos
- ✅ - October
- ✅ - Lazy
- ✅ - Sneaky
- ✅ - Haircut
- ✅ - Europa
- ✅ - Nineveh
- ✅ - Apocalyst
- ✅ - SolidState
- ✅ - Node
- ✅ - Enterprise
- ✅ - Jeeves
- ✅ - Inception
- ✅ - FluxCapacitor
- ✅ - Chatterbox
- ✅ - Aragog
- ✅ - Bart
- ✅ - Stratosphere
- ✅ - Celestial
- ✅ - Silo
- ✅ - Poison
- ✅ - Canape
- ✅ - Olympus
- ✅ - TartarSauce
- ✅ - DevOops
- ✅ - Hawk
- ✅ - Waldo
- ✅ - SecNotes
- ✅ - Giddy
- ✅ - Ypuffy
- ✅ - Carrier
- ✅ - Vault
- ✅ - Redcross
- ✅ - Lightweight
- ✅ - Chaos
- ✅ - Querier
- ✅ - Arkham
- ✅ - Unattended
- ✅ - Luke
- ✅ - Jarvis
- ✅ - Craft
- ✅ - Bitlab
- ✅ - Wall
- ✅ - Json
- ✅ - AI
- ✅ - Sniper
- ✅ - Mango
- ✅ - Obscurity
- ✅ - Monteverde
- ✅ - Book
- ✅ - Cascade
- ✅ - Magic
- ✅ - Cache
- ✅ - Fuse
- ✅ - SneakyMailer
- ✅ - OpenKeyS
- ✅ - Worker
- ✅ - Passage
- ✅ - Jewel
- ✅ - Bucket
- ✅ - Time
- ✅ - Ready
- ✅ - Tenet
- ✅ - Ophiuchi
- | Torrent Hoster
- | Drupal 7
- | Wordpress
- | php lavarel, sql injection
- | OctoberCMS
- | cookie authentification padding abuse
- | udp snmp ipv6
- | php rce, GNU screen 4.50
- | europacorp v0.2b, sqlmap, RCE
- | phpLiteAdmin v1.9, hydra port knocking
- | wordpress, wordlists
- | james smtpd, james pop3d
- | myplace nodejs api, mongodb, binexp
- | php sql inj, joomla, wp, binexp
- | askjeeves, kdbx, rdesktop
- | dompdf, webdav, pivot
- | Fuzzing
- | AChat, Win7
- | xml-content XXE, wordpress
- | server monitor, simple chat User-Agent
- | OGNL RCE, mysql, python lib hijacking
- | Node.js concatenating deserialization
- | Oracle DB RCE
- | FreeBSD, php LFI
- | cPickle, couchDB, pip
- | xdebug 2.5.5, airgeddon, knock, docker
- | Wordpress, gwolle-gb, tar
- | XXE, github repository enumeration
- | aes-256-cbc, ssh tunnel, H2 database
- | Evasive LFI, Container, cap_dac_read_search
- | XSRF, SQLi, nc.exe, smb, IIS,
- | SQLi, xp_dirtree, Ubiquiti UniFi-Video
- | FreeBSD, ldap, smb, putty, ssh certificates
- | Lyghtspeed, Quagga v0.99, BGP routes MITM
- | SOCKS5 Port Forwarding, double pivoting, gpg
- | SQLi, PHPSESSID, cmd injection, psql, sudo gid
- | LDAP, getcap, tcpdump, binary capabilities
- | WebMin, roundcube, ajax.php, LaTeX, firefox
- | smb, excel macros, mssql, xp_dirtree, winRM
- | smb, LUKS, javax.ViewState, powershell privesc
- | 2nd order blind SQL injection, luks initrd.img
- | Boostrap4, JWT, Ajenti, FreeBSD amd64
- | SQL Injection, python privesc, systemctl SUID
- | Gogs, REST api, docker, mysql sqlAlchemy
- | Gitlab, hardcoded creds in js, sudo git pull
- | Centreon, uncompyle, linpeas, GNU Screen 4.5.0
- | Json.Net deserialization, WS2012 R2 Datacenter
- | Speech recognition SQL injection, jdwp
- | RFI, MS Compiled HTML Help
- | MongoDB NoSQL injection, jjs
- | Python exec(), file decryption, background processes
- | Azure AD Connect exploit PoC
- | SQL Truncation attack, logrotten
- | ldap, VNC hardcoded key, AD Recycle Bin group
- | Magic bytes, mysqldump, PATH priority binary exec
- | OpenEMR, SQL Injection, memcached, docker mount
- | PaperCut Print Logger, SeLoadDriverPrivilege
- | Phishing via SMTP (yes), pypi, pip3
- | /usr/libexec/ld.so, OpenBSD, xlock
- | svnserve, Azure Devops Git repository
- | CuteNews, USBCreator DBus
- | rails 5.2.2.1, sudo 2FA (oath), gem
- | LocalStack (AWS), pd4ml
- | Jackson json parser deserialization, SQL SHELLEXEC
- | Gitlab CE 11.4.7, Docker Container escape
- | PHP deserialization, Race Condition bash exploit
- | YAML Java deserialization, wasm wat
Hack The Box - Hard Boxes
- ✅ - Joker
- ✅ - Calamity
- ✅ - Charon
- ✅ - Shrek
- ✅ - Mantis
- ✅ - Kotarak
- ✅ - Tally
- ✅ - CrimeStoppers
- ✅ - Falafel
- ✅ - Dropzone
- | Sudoedit Wildcards, Symlinks
- | PHP Injection, wav file, alpine privesc
- | SQL Injection, SuperCMS, SUID 4000
- | mp3 Spectogram, ECC Crypto, chown wildcard
- | IIS7, Orchard, DBeaver, MSSQL Server, psexec
- | Apache Tomcat, NTDS, disk group, lxc
- | hashcat on kdbx, smb mounting, xp_cmdshell
- | PHP base64 LFI, PHP zip RCE, apache logs, modrootme
- | linux char limit, video+disks group, linpeas
- | manual psexec, MOF, nc.exe, ADS, streams.exe
Recurrent Tricks
- ✅ - File transfers
- ✅ - reverse shells with XC
- ✅ - SSH Tunnels
- ✅ - Intercepting HTTP and HTTPS requests with Burpsuite
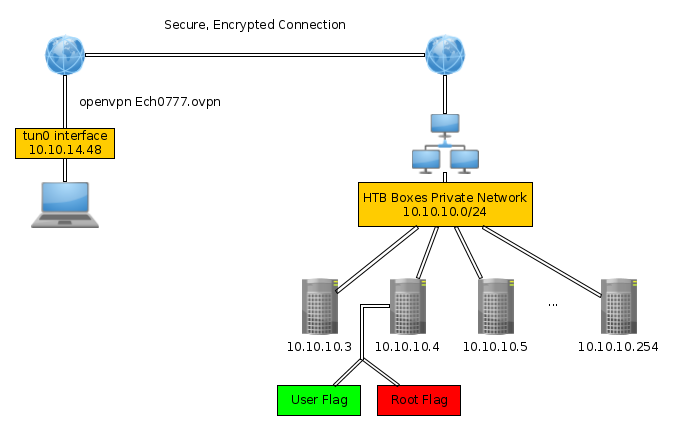
The Concept
The Goal is to capture both the User and the Root flags by gaining unauthorized access to the machines on HTB's private network, in order to get the flags, one has to employ various sets of pentesting skills, from finding out common vulnerabilities in the easier boxes, to crafting custom-exploitation for the harder boxes.
Binary Exploitation
gdb, gef, ghidra, pwntools, assembly, C, 32-64bit binaries, reverse engineering, CTF challenges