5.4 KiB
| author | date | gitea_url | xmr |
|---|---|---|---|
| cynthia | 2025-06-01 | http://git.nowherejezfoltodf4jiyl6r56jnzintap5vyjlia7fkirfsnfizflqd.onion/nihilist/blog-contributions/issues/311 | 84ybq68PNqKL2ziGKfkmHqAxu1WpdSFwV3DreM88DfjHVbnCgEhoztM7T9cv5gUUEL7jRaA6LDuLDXuDw24MigbnGqyRfgp |
DoT, DoH, DNSCrypt, DNS over Tor and Local DNS: What actually protects you? (and tutorials on how to set each of them up)
DNS is the most common way to resolve domain names into IP addresses. It's a pretty old protocol that still works, albeit with some shortcomings that have plagued the protocol over the years. The protocol lacks any encryption which allows any 3rd party with access to your connection (such as your ISP, etc.) to easily spy on DNS queries or even intercept and replace DNS responses to sabotage access to certain websites. Several solutions have popped up over the years to fix these issues, These mostly just act as wrappers around the DNS protocol in a way. This blogpost will measure the advantages and disadvantages of these solutions, and also offer a guide on how to set up each of them. This blogpost includes: DNS over TLS (DoT), DNS over HTTPS (DoH), DNSCrypt, DNS over Tor/DNS over VPN and Local DNS
Introductions to all the DNS protocols
DNS over TLS (DoT)
DNS over TLS is (one of) the first RFC-standard DNS encryption wrappers, wrapping the protocol around the Transport Layer Security, other than that, it's fairly simple. The problems that it has is that it has its own standard port number, which makes it easy to tell to a 3rd party that you are using DNS over TLS, and that it's slower, since it has to run over TCP rather than UDP.
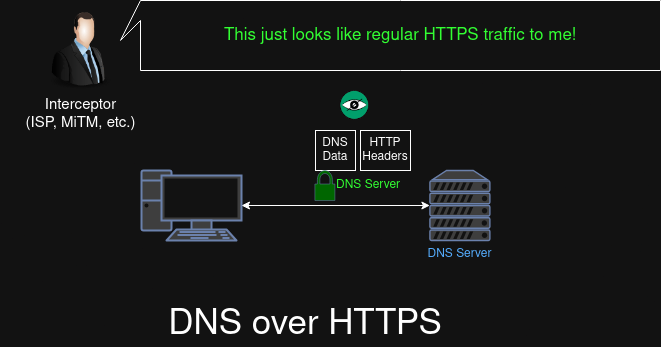
DNS over HTTPS (DoH)
DNS over HTTPS is the more newer RFC-standard DNS encryption wrapper, which wraps the protocol around HTTPS and uses 443 on TCP. The benefits are about the same as DNS over TLS, except that the fact that DNS is transmitted over HTTPS makes the protocol much harder to block than DNS over TLS (DoT) due it blending in with regular HTTPS traffic. ISPs and DPIs have to resort to blocking IPs associated with common DoH servers (which does not block DoH as a whole).
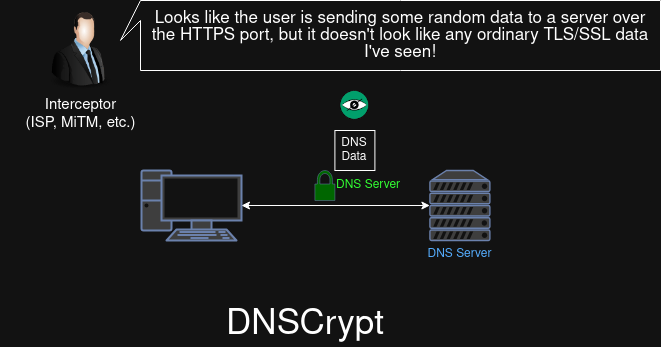
DNSCrypt
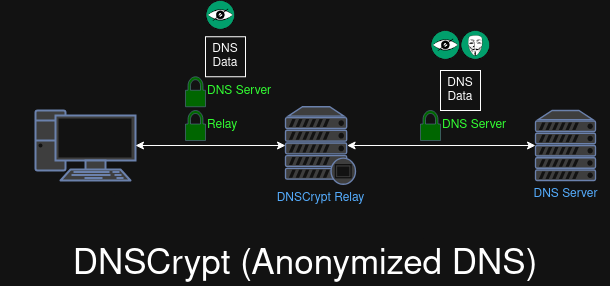
DNSCrypt is the oldest DNS encryption wrapper protocol, It is more optimized for speed than DoT and DoH and uses 443 on TCP/UDP (same port as HTTPS). The port number helps obfuscate the protocol at a basic level from ISPs and other MiTMs from detecting the usage of the protocol (although it won't help against DPIs). DNSCrypt also has a feature called Anonymized DNS which we will be talking in the next sub-section.
Anonymized DNS
(TODO)
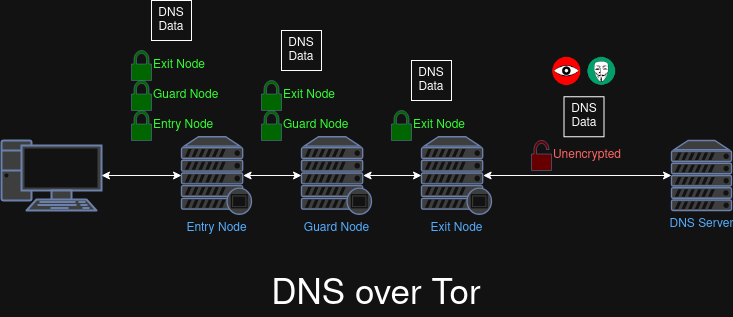
DNS over Tor
(TODO)
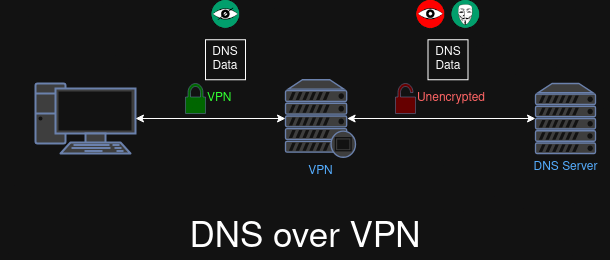
DNS over VPN
(TODO)
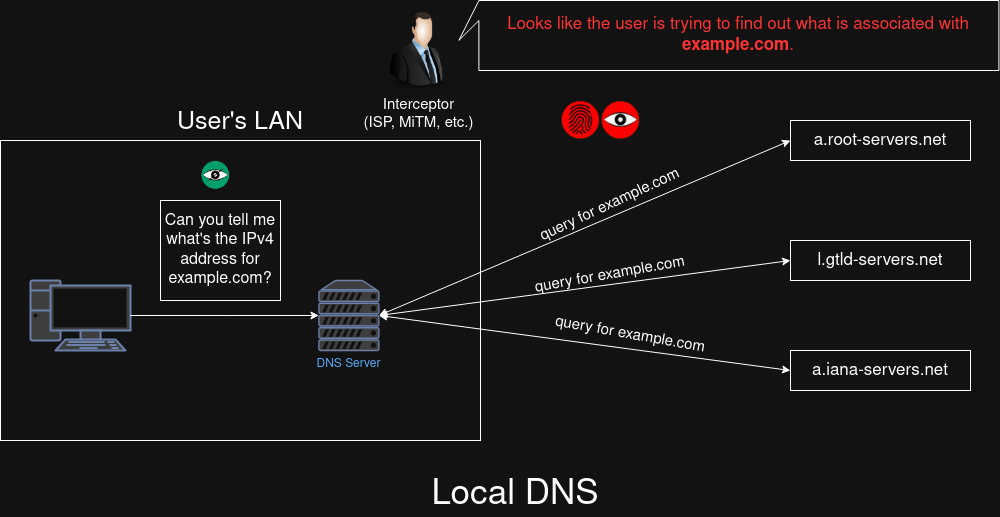
Local DNS
(TODO)
DNS protocol ratings
First of all, if we were to figure out which of these protocols protects us, we'll need some way to measure how well they perform. We will be measuring each of the following abilities:
- Security: Whether the DNS queries and responses are fully end-to-end encrypted (from user to the DNS server, including the Tor nodes/VPN node in-between)
- Detectability: Whether a 3rd party adversary (such as the user's ISP) can detect and distinguish usage of the protocol from the rest of the user's traffic.
- Anonymity: Whether the protocol offers anonymity protection for the user.
| Abilities | DNS over TLS | DNS over HTTPS | DNSCrypt | DNS over Tor/VPN | Local DNS |
|---|---|---|---|---|---|
| Security | ✅ The protocol uses TLS between the user and the DNS server. | ✅ The protocol uses TLS or SSL between the user and the DNS server. | ✅ The protocol uses a custom encryption protocol between the user and the DNS server. | ✳️ Although the connection between the user and the Tor node/VPN is encrypted, DNS is unencrypted so the exit node or VPN server can see queries and responses | ❎️ Although a 3rd party adversary cannot intercept a local DNS server, they can look at the authoritative DNS queries that the server makes |
| Detectability | ❎️The protocol has its own standard port (853/TCP) which makes it super easy to detect for a 3rd party | ✅ The protocol blends in with HTTPS traffic, which makes it much harder to detect | ✳️ Although DNSCrypt listens on port 443 (UDP/TCP, the same port as HTTPS) which makes surface-level detection much harder, the use of a custom protocol may allow for detection on DPIs that are written to distinguish DNSCrypt's protocol from TLS/SSL protocol | ✅ A 3rd party adversary would not be able to detect DNS usage from the Tor/VPN traffic | ✅ The traffic from the local DNS server appears just like any other DNS query |
| Anonymity | ✳️ The protocol does not offer built-in anonymity protection, but it can be used over Tor. | ✳️ The protocol does not offer built-in anonymity protection, but it can be used over Tor. | ✅ DNSCrypt has a feature called Anonymized DNS, where instead of connecting to a DNSCrypt server directly, a user can connect through a relay DNSCrypt server to relay data over to that server. | ✅ Tor offers anonymity protection (maybe same thing for VPN but a little different) | ❎️ Unencrypted authoritative DNS queries (done by the local DNS server) can allow the user to be deanonymized by a 3rd party adversary |